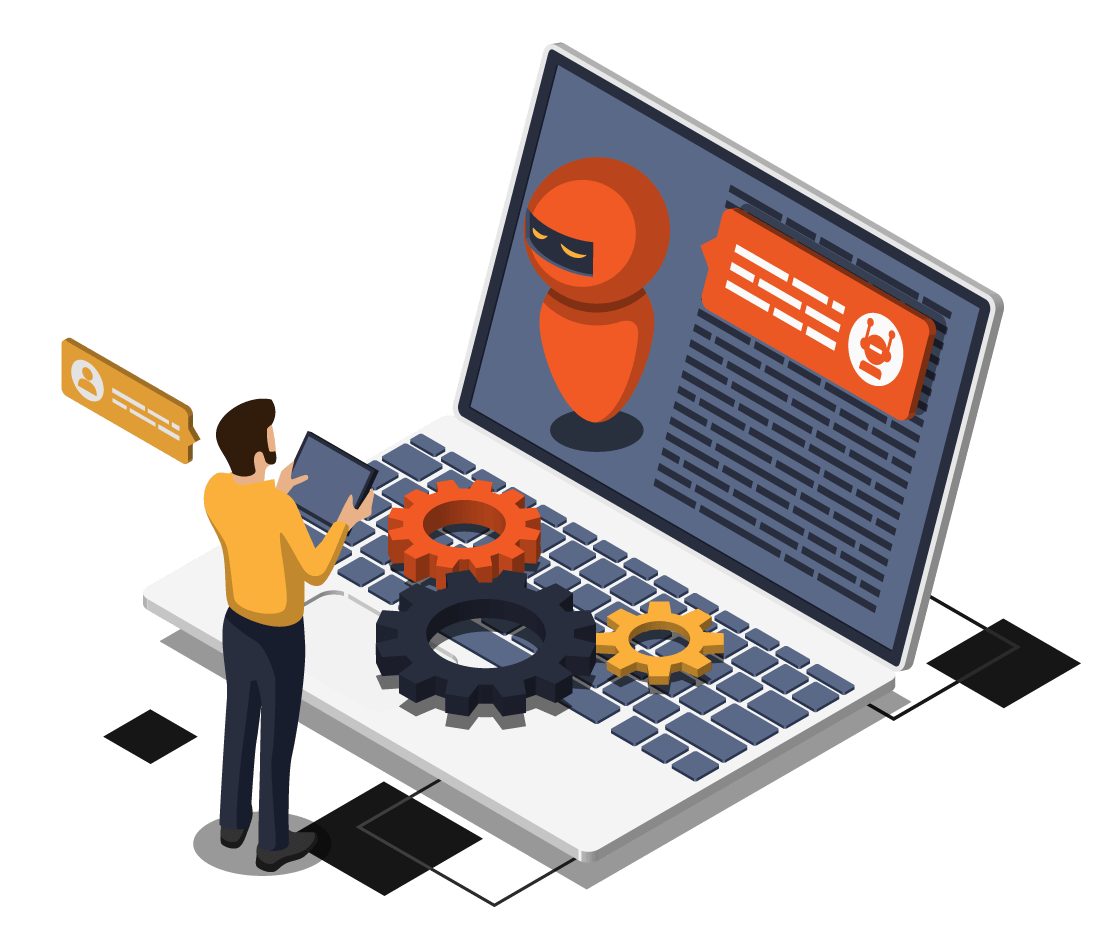
Involved in more than 200 industrial digital transformation projects over the last few years, Creative IT would like to share its experience with you in order to carry out your own project and allow you to benefit from it as soon as possible. We are talking about transformation because it is the whole activity of […]

Qubes, the MES for industries in motion!
The factory of the future is the connected factory. With Qubes, you streamline exchanges between production equipment, tools (IoT), operators and management IT around a single system for monitoring production activities.
With Qubes MES software, factory 4.0 is now !

Qubes 4Cloud
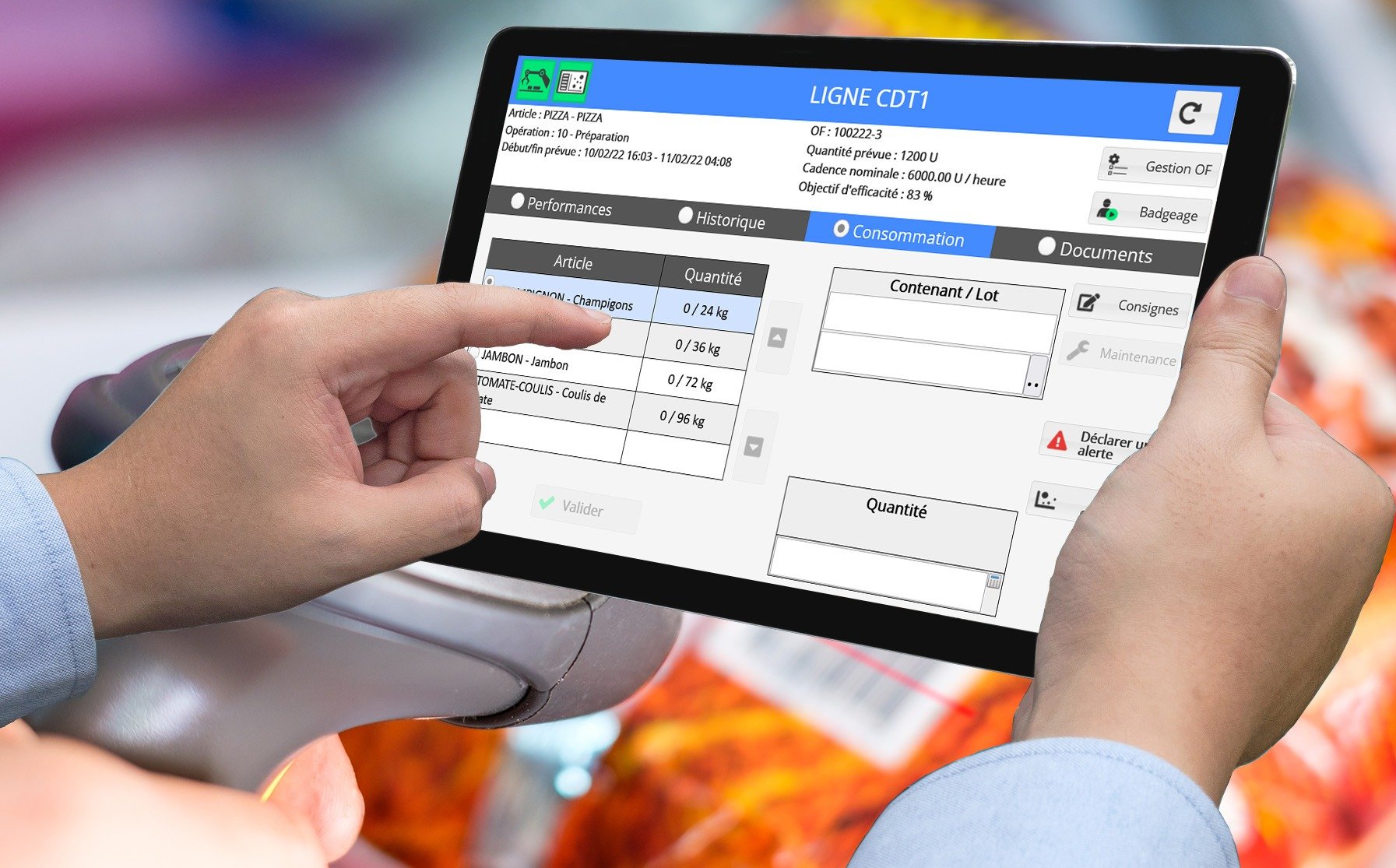
The strength of the Qubes 4Cloud solution lies in its ability to monitor your production activities in real time, with a controlled investmentc.
Augmented reality
A new way of formatting production data: process data, machine rates, quality rates, operating procedures; the information relevant to the user is displayed on the mobile terminal.
Big Data industriel
Pack Manufacturing Data Acquisition for Big Data
A software and hardware solution for data acquisition on your production lines for Big Data. A fast deployment, a scalable solution.
High availability of the information system
Creative IT is fully positioned in the Industry of the Future era, already offering operational solutions for connected factories.
Qubes i4 is an industrial device located in the factory and whose role is to ensure the digital continuity between the global Information System of the company and the flows of the production sites (production monitoring functions, machine automatons, connected objects): THE high availability solution.
Qubes i4
- High availability through real-time synchronization of plant data
- An application designed for production monitoring
- An industrial device in the plant synchronized to the central server
Master the digital continuity

How to connect the factory of the future to the information system?
Les
Industrial companies are carrying out their digital transformation. This is reflected in a strong technological evolution – automation and robotization of production, integration of
objects, product customization – but also by an unprecedented extension of the company’s
of the company’s information system. Each production machine and each finished product is potentially a communicating object to be connected.
Secure the production process
To respect the standards of your sector, to satisfy the requirements of your customers and to reduce the time to market, it is necessary to secure the data used by the machines, to allow the equipment to exchange between them, to inform the operator in real time of the modification of a plan…
The Qubes solution allows you to easily manage all the configuration files of your production equipment, to alert a department as soon as supplies are insufficient, to warn another workshop of the start of production…

Pour aller plus loin

White Paper – Factory 4.0
IoT, 3D printing, industrial Big Data: will all these new technologies reach the workshops?
- Discover the main technologies of the Industry of the Future and their concrete applications
- Evaluate if these technologies are adapted to your company
- Estimate the advantages and difficulties of implementation
- Study the different steps you could take
By providing an overview of the market for the main technologies of Factory 4.0, this white paper addresses the challenges related to the integration of these new technologies within production sites on various levels: economic, IT security, agility and change management.